Bypassing Cloudflare WAF and IP restriction (kind of)
Cloudflare is a popular choice for both individuals and corporates due to it’s capability to protect your website from various kinds of network and application attacks.
Methods of bypassing Cloudflare WAF
Essentially there are 2 ways of bypassing the WAF provided by Cloudflare:
- Customize the payload to previously unknown formats
- Getting the origin IP of the application.
I won’t discuss the first approach in this article, instead I’ll talk about the second one.
There are many ways for an attacker to obtain your IP address:
- Using historical DNS data
- Using SSL certificates fingerprints with intelligence services such as Censys and Shodan.
- Trigger a request from the server, either by functionality (pingback, upload image from url) or using an exploit (SSRF).
When one have the origin IP, just connect to that IP with the appropriate hostname and start poking, right?
Cloudflare knows this, and advises it’s customers to block all ingress traffic, sans it’s (IP ranges)[https://www.cloudflare.com/ips] on their reverse proxy or firewall.
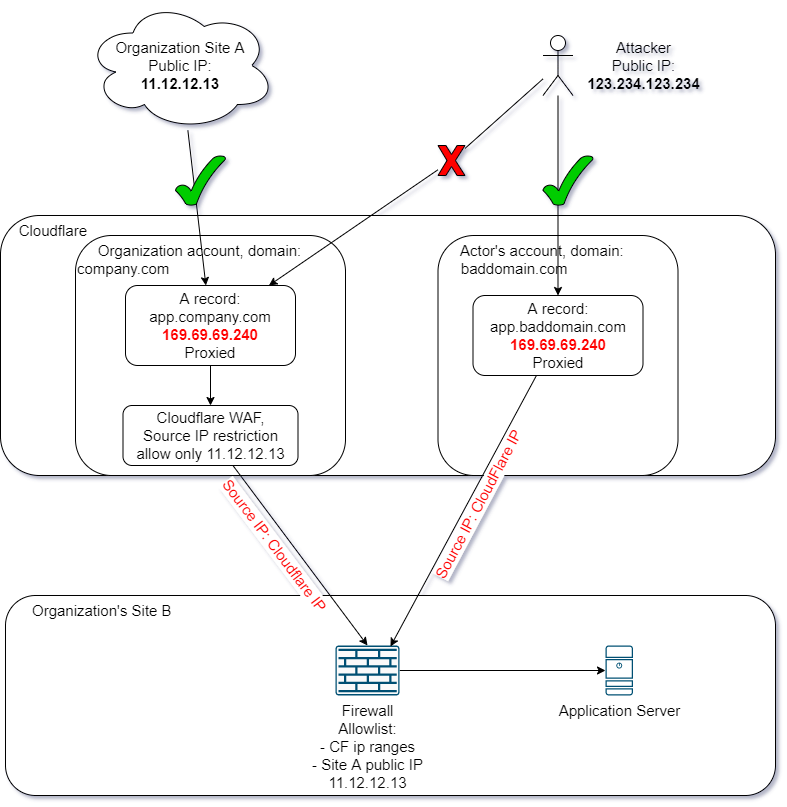
Sometimes that’s not enough! Some teams also put a policy on Cloudflare explicitly allowing certain IP addresses to connect to the service and deny the rest of the internet.
Critical mistake
If the application or the reverse proxy handling incoming requests to the website does not verify the hostname in HTTP requests, there is still a way to bypass the WAF and source IP restriction.
An attacker can create an A record on the Cloudflare DNS service pointing to the server’s original IP and set it to Proxied. In some cases this setup is equal to not having protections at all.
Due to the domain the attacker used not having any kind of WAF or IP restriction, they are able to access the application unimpeded.
Remediation
When switching from non-proxied DNS entry on Cloudflare to proxied, change the server’s IP if possible, this approach may only be applicable to organization using cloud infrastructures. Better to enable proxied mode when adding DNS records to avoid leakage due to DNS scrapping.
Prevention
Verify the hostname of incoming HTTP requests at the application layer or web server applications (nginx, Apache, traefik, CloudFront, etc).
Edit
Here is a very well-written and insightful article on the matter, the writer also created 2 tools for detecting and exploiting the issue.
Please go visit https://blog.ryanjarv.sh/2022/03/16/bypassing-wafs-with-alternate-domain-routing.html